Welcome to today’s blog.
In today’s post I will be discussing what a Tenant is within Azure Active Directory. I will also be explaining the purpose of a Tenant within Azure Active Directory and how it is used in the overall grouping and protection of application access for users within a Tenant within Azure Active Directory.
One of the key resources that are part of a tenant, are user accounts. It is these accounts that are required when we wish to authenticate users to the Azure Active Directory. Another key resource are applications, that are registered within the tenancy, and can be secured with access permissions and rights to the users within the tenancy. I will discuss these in more detail in the sections that follow.
What is an Active Directory Tenant?
A tenant is an organization that is an instance of Azure AD. Within the organization there are accounts, resources, applications. Most of us have used an on-premises Windows Active Directory environment where these resources are part of, so some of the same concepts still apply in terms of resources and security. In the Azure AD environment, the tenant is much like a container that is used to encapsulate the security for applications that are registered within the AD Tenancy. After an application is registered within an Azure AD Tenant, users within the tenancy can be given various rights to access the application, or even delegated access to other Azure applications such as MS Graph API through the application. In this case the application within tenant serves as a single-tenant application. When we give access to users outside of the tenant, the application serves as a multi-tenant application.
When you sign up for an Azure account, you are automatically a member of a default directory, which is a tenant within Azure AD, and you are an Administrator of your own tenancy.
When you subscribe to a service, such as MS Office 365, the MS account you used to sign up is automatically a member of a tenancy within Azure AD. However, the account is not automatically an Azure subscription member.
When you subscribe to a popular cloud or online based application service, you are a user that is part of a tenancy. Where there are many businesses subscribing for the service, each business is a tenant within a multi-tenancy. An example as I mentioned is MS Office 365, where there are not just individual consumers, but also organizations and schools with subscriptions, and the organizations and schools have in many cases their own tenancy. Where the service is provided for multiple tenants, the service is provisioned as a Software as a Service or SaaS. Where the service is provided to one organization, work or school, the service is a line of business application usually delivered as a PaaS application in Azure.
For this discussion you get some idea of what a tenant is in Azure.
Creation of a Tenant in Azure
To make things a little clear I will show how to create a basic tenant within Azure. To do this you will need to already have an Azure account. After you login to the Azure portal, select your default directory. It should look something like this:
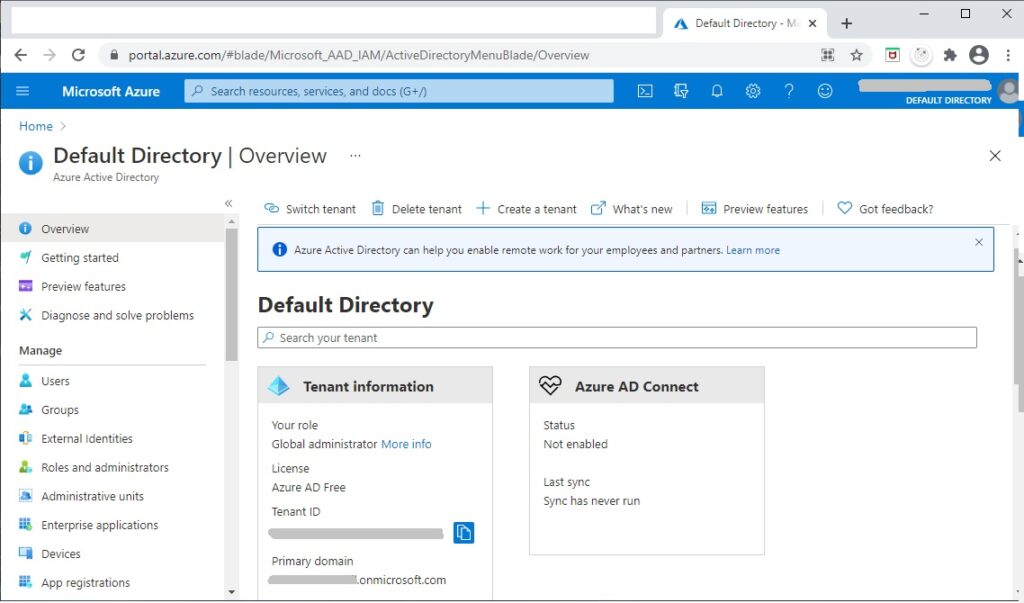
You will notice a few things:
- Your Default Directory is a Tenant.
- Your Default Directory has a Tenant ID.
- You are the Global Administrator of the Default Directory.
- The Tenant has a domain name in the form: [domain].onmicrosoft.com.
- You can manage Tenants: Create, Delete and Switch.
To create a tenant, click on the Create Tenant plus sign at the top.
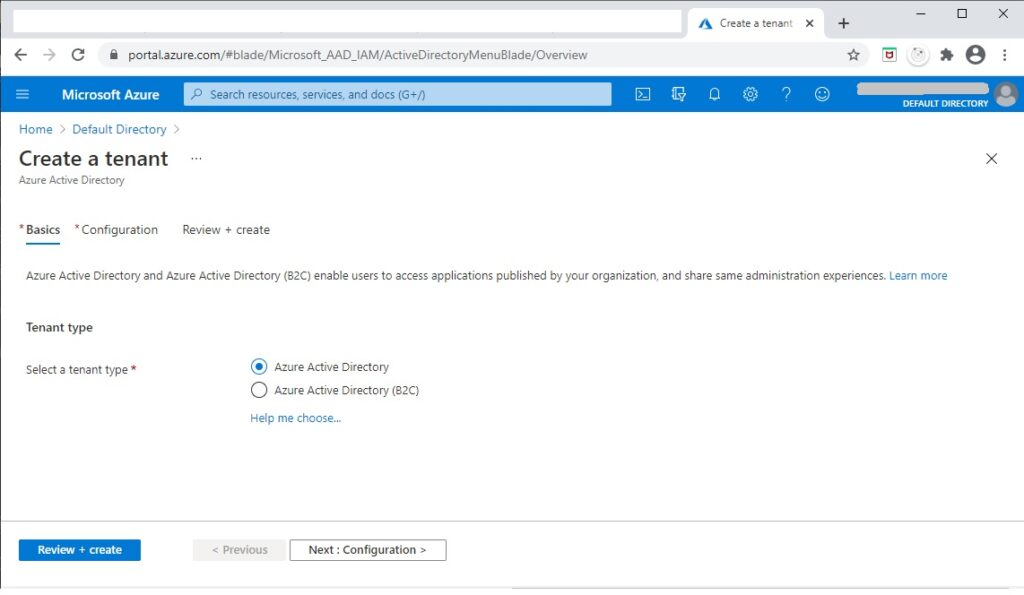
In the next screen you have two choices, Azure Active Directory and Azure Active Directory (B2C).
I will briefly explain what each is:
An Azure AD B2C tenant is used to provide accounts that are external and social media related such as web and mobile applications and social media including Facebook, Google etc. The security platforms used are external. All users are signed in with email accounts.
An Azure AD tenant is used to provide accounts that are for work, school and organizations including line-of-business single-tenant applications and multi-tenant SaaS based subscription applications. All users are signed in with an Azure account or a personal MS account.
A more useful FAQ on the differences is on the Microsoft Azure Active Directory site.
As I may be using this tenant to access other resources within Azure and sign in with an Azure account, I will choose to create an Azure Active Directory:
Next, there are three mandatory properties that need to be entered:
- Organization name
- Initial domain name
- Country/region
The domain name should never have any spaces or special characters.
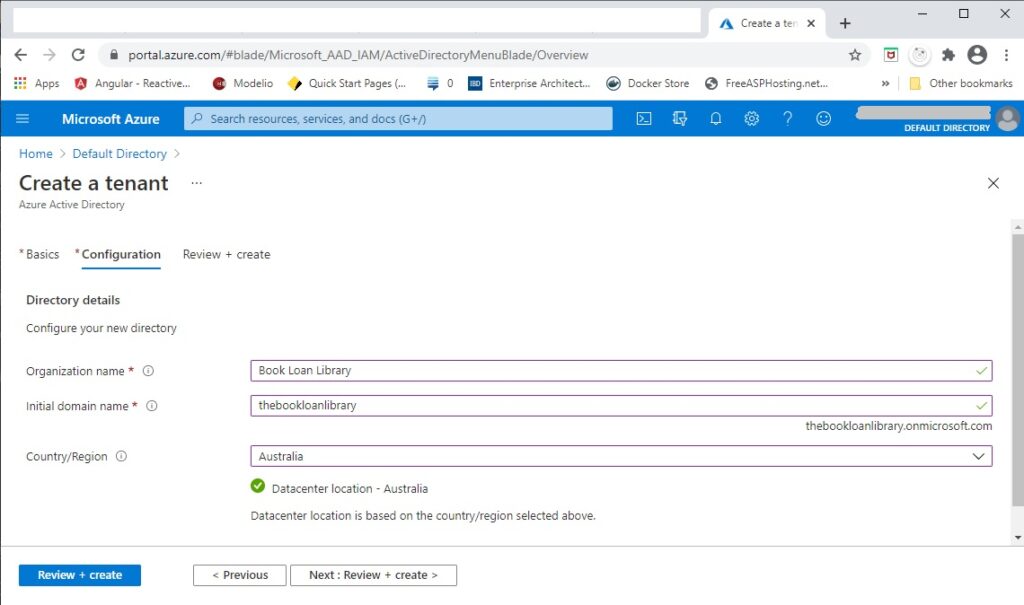
The next screen will validate the details. Once validated, create the Tenant.
After creation you will be provided with a Tenant ID and a primary domain which can be used to provide for future access to registered applications within the tenancy:
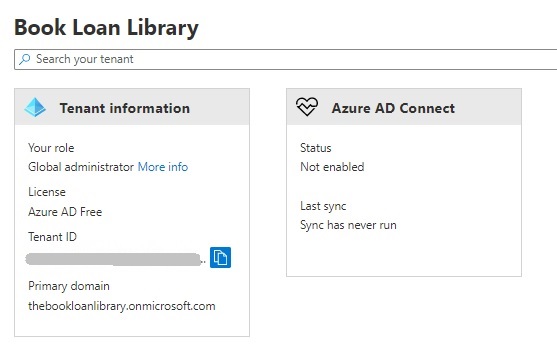
Well done. We have just created an Azure AD Tenant!
This is just the starting point. From here you can add additional users to the tenancy and register applications such as web client, SPA client, web API services. We can then provide access to our applications to our users and use our applications to delegate sign-in user access to other resources such as MS Office 365 applications (if we also have a subscription for MS Office 365) and MS Graph API to access other applications such as Outlook, Calendar, OneNote, Excel and so on.
In future posts I will be exploring how we can use an Azure AD Tenant to secure access to registered applications and how to sign-in to Azure AD from client web applications and web API services.
That is all for today’s post.
I hope you found this post useful and informative.
Andrew Halil is a blogger, author and software developer with expertise of many areas in the information technology industry including full-stack web and native cloud based development, test driven development and Devops.


